What is Encryption?
Schedule V of the Information Technology (Certifying Authorities) Rules, 2000, defines encryption as- “The process of transforming plaintext data into an unintelligible form (cipher text) such that the original data either cannot be recovered (one-way encryption) or cannot be recovered without using an inverse decryption process (two-way encryption).” Cryptographic techniques are generally used to control access to critical and sensitive data/information in transit and storage on the internet.
What is SSL (Secure Socket Layer) Encryption?
SSL is a standard security technology for establishing an encrypted links between a server and a client—typically a web server (website) and a browser (Mozilla, Chrome, etc.); or a mail server and a mail client.[1] It allows personal and sensitive information (credit/debit card numbers, social security numbers, passwords, etc.) to be transmitted securely. Usually, data/information sent between browsers and web servers is sent in the form of plain text which makes such data/information quite vulnerable to unauthorized interception. In other words, if a hacker is somehow able to intercept the data being sent between a browser and a web server, he may be able to see and use such information being passed between the website and the browser. The reason why it is so important is that it creates a trusted environment where user can feel secure about the personal and sensitive information they pass on the internet while making online purchase, sending confidential data, etc. It should, however, be noted that SSL does not provide end-to-end encryption security at the application layer but is only designed to encrypt data in transit at the network transport layer.[2]
Why is SSL Certificate needed?
In order to establish a secure connection, the browser and the web server may need an SSL Certificate. As of today, Extended Validation Secure Sockets Layer (EV-SSL) Certifications are increasingly being used for such purposes these days. It is to be noted that SSL Certificates do not dictate what key size is used.[3]
Types of Encryption
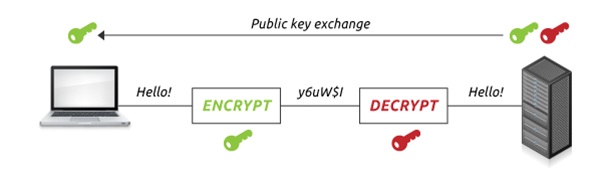
Asymmetric Encryption: Asymmetric encryption (aka public-key cryptography) uses separate keys for encryption and decryption. Although, encryption key (public key) can be used by anyone to encrypt a message, decryption keys (private keys) are kept secret to ensure that it is only the intended receiver who can decrypt the message. Schedule V of the Information Technology (Certifying Authorities) Rules, 2000 defined public key cryptography as- “A type of cryptography that uses a key pair of mathematically related cryptographic keys. The public key can be made available to anyone who wishes to use it and can encrypt information or verify a digital signature; the private key is kept secret by its holder and can decrypt information or generate a digital signature.” Asymmetric keys are typically 1024 or 2048 bits. However, keys smaller than 2048 bits are no longer considered safe to use. [4]
Image from here
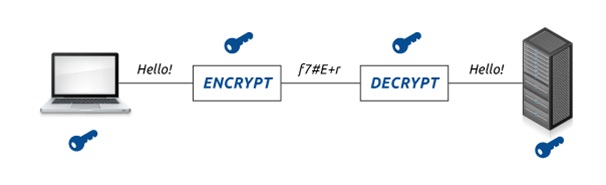
Symmetric Encryption (or pre-shared key encryption): Such encryption uses a single key for both encryption and decryption of data. Here, both the sender and the recipient need the same key to make a communication. Symmetric keys, being smaller in size, pose lesser computational burden.
These key sizes are generally in the range of 128 or 256 bits.
Image from here
It is also to be noted that the larger the key size, the harder it is to crack the key. Since asymmetric keys are bigger than symmetric keys, data that is encrypted asymmetrically is tougher to crack than data that is encrypted symmetrically.
Laws on Encryption Limits
As of today, India does not have any clear and well established laws and policies regarding encryption or encryption techniques to secure electronic communication. The extant laws only prescribe for use of such encryption standards or algorithms which are well established and in conformity with the international standards.
As per Rule 5.2(6) of the Information Technology (Certifying Authorities) Rules, 2000 (“Rules”), electronic communication systems used for transmission of sensitive information can be equipped or installed with suitable encryptor or encryption software. Similarly, Rule 5.3(1) of these Rules provides that any highly sensitive information or data should be in an encrypted format to avoid compromise by unauthorized persons. The Government has the power to determine the manner of encrypting sensitive electronic records requiring confidentiality. Amendment to the Information Technology Act, 2000 in the year 2008 provides that the Government can prescribe the modes or methods for encryption for secure use of the electronic medium and for promotion of e-governance and e-commerce.
In addition, there are specific encryption limits provided by RBI, SEBI and Dept. of Telecommunications (“DoT”). As per RBI, for all banking transactions, normally, a minimum of 128-bit SSL (Secure Socket Layers) encryption is expected. SEBI prescribes a 64-bit/128-bit encryption for standard network security and mandates the use of encryption technology for security, reliability and confidentiality of data.
DoT requires an ISP to restrict the level of such encryption for individuals, groups or organizations to a key length of only 40 bits in symmetric key algorithms or equivalents. Information Technology (Certifying Authorities) Rules, 2000 requires ‘internationally proven encryption techniques’ to be used for storing passwords.
In order to provide internet services in a particular service area, an ISP (“Licensee”), is required to enter into a License Agreement with the Govt. of India through DoT (“Licensor”). Some of the mandatory conditions that ISP, as a Licensee, is required to abide by, under this License Agreement are –
- The Licensee shall ensure that bulk encryption is not deployed by them at any point. Further, Individuals/ Groups/ Organizations are permitted to use encryption up to 40 bit key length in the symmetric key algorithms or its equivalent in other algorithms without obtaining permission from the Licensor. However, if encryption equipments higher than this limit are to be deployed, individuals/groups/organizations shall obtain prior written permission of the Licensor (Government of India through DoT) and deposit the decryption key, split into two parts, with the Licensor.[5]
- The Licensee shall not employ bulk encryption equipment in its network. However, the Licensee shall have the responsibility to ensure protection of privacy of communication and to ensure that unauthorised interception of message does not take place.[6]
Procedure for obtaining written approval for the usage of bulk encryption key
The Company needs to abide by the aforesaid encryption limit of 40 bits imposed on the ISP under the License Agreement. However, if the Company needs to use an encryption level of more than 40 bits, it should make an application before the Deputy Director General (Security/ AS-II) of DoT, Govt. of India through registered post with the complete details of the applicant Company and an undertaking to submit the decryption key with the DoT. Further, it is to be noted that there are no specific procedure provided for making such an application and a waiver can be obtained only with prior permission of DoT unless it has been specifically approved by them.
Conclusion
As of today, India desperately needs a well established encryption/decryption framework in order to address the concerns of both information technology industry and law enforcement agencies in the light of cyber security, privacy and national security. Today, the private sector is required to constantly adapt and evolve with the technology to deploy stronger encryption on their networks to ward off disruptive cyber security threats/attacks. In this regard, their ability to combat cyber security threats and to protect their technological infrastructure against such threats depends mostly on presence of a clear national framework or regulatory environment. It is also important that any regulation dealing with encryption should not require the private parties to make a choice between either weaker encryption or the burden of giving prior notice and decryption key escrow for stronger encryption. Such a requirement, especially for an Internet Service Provider may prove to be too onerous in the sense that it can create a disincentive for such private players to deploy robust encryption which will eventually contribute to India’s vulnerability to cyber attacks. It is to be noted that the requirement of notice and deposit are usually the norm in other jurisdictions. Therefore, any regulations regarding encryption provided by the Government should be flexible and adaptive to constant innovations in encryption technology. Also, the Government must ensure that any encrypted communications or data should not pass through any third party or government’s agent who may derive benefits from such encrypted communications.
Image from here
[1] “What Is SSL (Secure Sockets Layer) and What Are SSL Certificates?” available at https://www.digicert.com/ssl.htm
[2] RBI Report dated 21.01.2011
[3] “Behind the Scenes of SSL Cryptography”, available at https://www.digicert.com/ssl-cryptography.htm
[4] Supra Note 3
[5] Condition 2.2(vii) in Part-I of the Schedule to the License Agreement
[6] Condition 32.1 in Part-I of the Schedule to the License Agreement